Microsoft released a rolling upgrade of Windows 10 in October 2017. The “Fall Creators” edition (version 1709, codename Redstone 3) contains a new feature called “Controlled Folder Access”, which is designed to combat ransomware attacks.
Controlled Folder Access is part of Windows Defender Security Centre that works with Windows Defender Anti-Virus to prevent “suspicious” executable files, DLLs, and scripts from writing to (or encrypting) files within certain folders.
What folders are protected?
While additional folders can be added, the following locations will always be monitored when Controlled Folder Access is enabled:
- User: Documents, Pictures, Videos, Music, Desktop, Favorites
- Public: Documents, Pictures, Videos, Music, Desktop
How does Windows determine what `suspicious’ code is?
It’s what Windows Defender Anti-Virus identifies. As such Controlled Folder Access relies on Windows Defender Anti-Virus to be running.
What about application false positives?
It may be the case that legitimate applications are incorrectly flagged by Windows Defender Anti-Virus as being `suspicious’ preventing or hindering legitimate use. Such applications can be white-listed.
To facilitate this, Controlled Folder Access supports an `audit’ mode, where an event is generated when the application would normally be prevented from writing to a protected folder. Those events can be reviewed to identify legitimate applications that can be added to the white-list.
Is Controlled Folder Access enabled by default? How do I configure it?
Controlled Folder Access is not enabled by default and can be configured via:
- The User Interface
- Group Policy (a Group Policy would need to be configured on a system that contains the correct administrative templates for the options to be available for selection): Computer Configuration > Administrative Templates > Windows Components > Windows Defender Anti-Virus > Windows Defender Exploit Guard > Controlled Folder Access
- Manual Registry modification (i.e. via a script)
- PowerShell cmdlets:
Set-MpPreference -EnableControlledFolderAccess [Enable | Disable | Audit] Add-MpPreference -ControlledFolderAccessProtectedFolders c:\path\to\protect,c:\other\path Remove-MpPreference -ControlledFolderAccessProtectedFolders c:\path\to\no\longer\protect
Note: Set-MpPreference can also be used to specify folder items but will clear the list first, whereas Add-MpPreference adds to the list.
What Registry keys are used by Controlled Folder Access?
Is Controlled Folder Access enabled?
Registry path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exploit Guard\Controlled Folder Access Registry Key: GuardMyFolders Key Type: REG_DWORD Key Value: 0
Protected Folders
Registry path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exploit Guard\Controlled Folder Access\ProtectedFolders Registry Key: audit Key Type: REG_DWORD Key Value: 0
To specify protected folders:
Registry path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exploit Guard\Controlled Folder Access\ProtectedFolders Registry Key: Full path to protect, i.e. c:\test Key Type: REG_DWORD Key Value: 0</code>
What can be protected? Any limitations?
Network shares and mapped drives can be protected, but Controlled Folder Access does not support the use of:
- Environment Variables
- Wildcards
- The Windows drive (typically C:\)
Seriously, don’t protect the entire Windows drive as Windows will be unable to function correctly and strange behaviour will result.
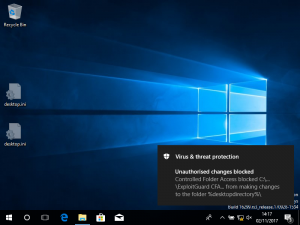
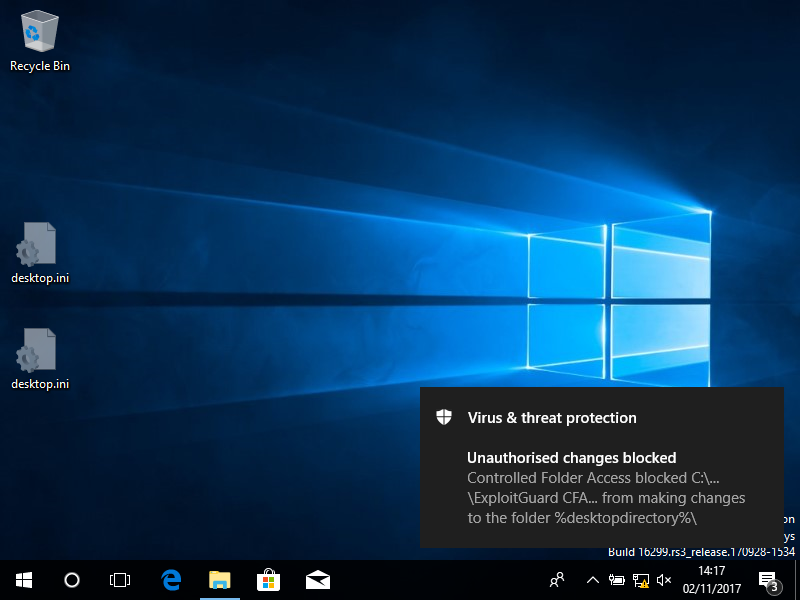
What happens when write access is blocked?
A notification is displayed that provides the path of the executable that was blocked, and the path of protected folder that the write attempt was for. This information is also recorded in the event log, using the following event values:
- Event ID: 5007: Event when settings are changed
- Event ID: 1124: Audited Controlled folder access event
- Event ID: 1123: Blocked Controlled folder access event
The following image shows the notification of a write action being blocked:
Can the blocked write notification message be customised?
Yes, at least for Enterprise environments. Providing details of who to contact (service desk, IT Security, etc.) can be included in the notification message via the following Group Policy settings:
Computer Configuration > Policies > Adminstrative Templates > Windows Components > Windows Defender Security Center > Enterprise Customization
- Set “Configure customized contact information” to “Enabled”
- Set “Configure customized notifications” to “Enabled”
- Set “Specify contact compant name” to “Enabled” and add the company details
- Enable and set at least one of the following:
- “Specify contact email address or EmailID”
- “Specify contact phone number or Skype ID”
- “Specify contact web site”
Does Controlled Folder Access work with third-party Anti-Virus applications?
No, or at least not in the tests performed when writing this post. Controlled Folder Access requires the use of Windows Defender Anti-Virus to be active.
Most third-party Anti-Virus solutions replace existing products, and attempting to run multiple Anti-Virus solutions at the same time can significantly hinder system performance, or even lead to each one preventing the other from being able to scan files or removable drives which could lower protections. One Anti-Virus program might flag others as being infected (i.e. triggering on the detection patterns) or malicious, and quarantine key files – potentially breaking that product.
How can I tell Controlled Folder Access and Notifications are configured and working?
Microsoft have produced an ExploitGuard CFA File Creator tool to trigger Controlled Folder Access actions, which causes notifications to be displayed.
Details on the ExploitGuard CFA Demo Tool, and a link to download it, can be found on Microsoft’s web site.
Conclusion
For home users or business that do not have a corporate Anti-Virus solution, Windows Defender Anti-Virus and Controlled Folder Access will be better than nothing.
However, larger businesses typically have existing enterprise-wide Anti-Virus solutions in which significant time and effort (and money) has been invested. It would be difficult to convince the IT Security teams of such companies to throw out that investment, so I don’t expect Controlled Folder Access to be used much in large businesses.
Controlled Folder Access is a new feature, and it may be that Microsoft modify it to work with third-party Anti-Virus products in the future.