The Bash Bunny is the most recent attack tool released by Hak5 for use by penetration testers. Although the primary focus of the tool is red/black/purple team engagements, it is a dynamic device allowing reconfiguration to suit the scope of work.
The Bash Bunny is a Human Interface Device (HID), ethernet & mass storage attack tool all packaged up into one device which allows for multiple types of attack to be performed in same payload.
Payloads are primarily written in Bash Scripts and there is also support for the previous Ducky Scripts that are used for the USB Rubber Ducky and there is no longer an encoder needed as all the payloads are written in text files.
Additional tools (such as Responder and Nmap) can also be installed on the inbuilt 8GB SSD storage.
Strong considerations should be made in regards to situations in which the Bash Bunny is used. For example, it takes approximately 7 seconds for the device to initialise prior to executing the payload. Therefore, advance knowledge of the target systems would greatly reduce the need of having to avoid reconfiguring payloads in the midst of the attack.
When performing data extraction using the Bash Bunny, consideration should also be taken into account with the amount of time that files take to transfer and the amount of space that will be consumed. In order to switch payloads, the Bash Bunny needs to be unplugged from the victim machine and as a result, an additional 7 seconds will be required for for reinitialisation – so you may need to stall victims slightly longer!
What are Bunny Scripts?
Bunny Script is text-based language that provides inbuilt commands specific to the hardware that can be used alongside standard bash scripting. Ducky Script can also be used without an encoder and can be stored in separate files for easy management of payload elements. Additional platform scripts can be used and executed as well these can include PowerShell, batch files and shell scripts.
Key elements of Bunny Scripts
Attack Modes:
- RNDIS_ETHERNET (Windows)
- ECM_ETHERNET (Mac/Linux)
- STORAGE
- SERIAL
The attack modes tell the device what functionality to enable upon initialization. You can use multiple modes at the same time.
LED usage can assist you at a glance to know the status of your attack and when it is safe to remove the device upon completion, there are multiple options for these from simple colours to complex patterns.
Serial console
The Bash Bunny features a dedicated serial console from its arming mode. From serial, its Linux shell may be accessed.
On Linux this will be:
sudo screen /dev/ttyACM0 115200</code> or <code>sudo screen /dev/ttyUSB0 115200
On OS X this will be:
sudo screen /dev/tty.usbmodemch000001 115200
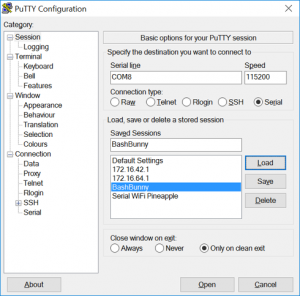
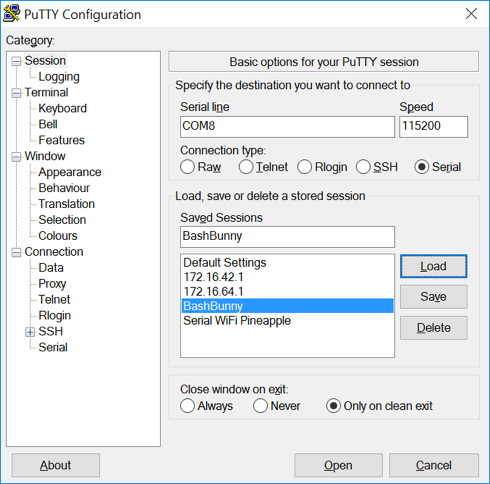
On Windows, you need to find the COM# use PowerShell and the following:
[System.IO.Ports.SerialPort]::getportnames()
Then use Putty or similar tool to connect to the COM Port:
Ethernet mode
As we have already mentioned, one of the main uses of the Bash Bunny is as a hardware implant for use during red team engagements. In such scenarios, allowing your Bash Bunny and main testing device to share an Internet connection can be very useful. For Linux, Hak5 provide a useful script to assist with this which can be found here:
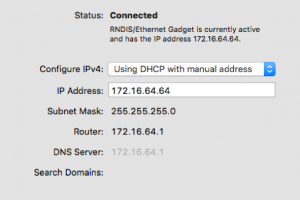
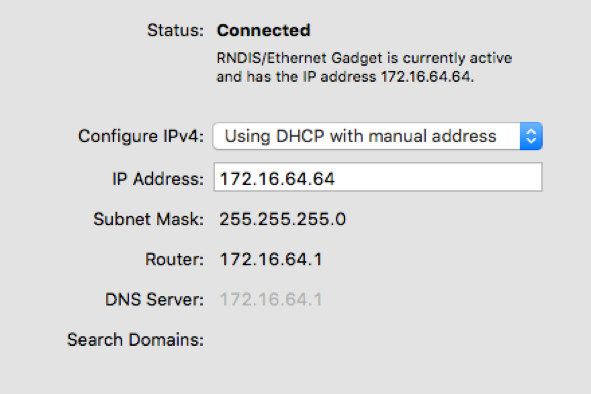
A similar approach can be taken when your main testing device uses OS X, however this requires some manual steps to be performed as below:
Firstly, configure a payload.txt with the following:
ATTACKMODE ECM_ETHERNET
Internet sharing is easy with the Sharing tab in system preferences. I selected sharing WiFi (or select how you’re connected to the internet) with the RNDIS/Ethernet Gadget and then executed the following commands:
defaults write /Library/Preferences/SystemConfiguration/com.apple.nat NAT -dict-add SharingNetworkNumberStart 172.16.64.10 defaults write /Library/Preferences/SystemConfiguration/com.apple.nat NAT -dict-add SharingNetworkNumberEnd 172.16.64.200 defaults write /Library/Preferences/SystemConfiguration/com.apple.nat NAT -dict-add SharingNetworkMask 255.255.255.0 defaults read /Library/Preferences/SystemConfiguration/com.apple.nat
SSH access in ethernet mode
SSH access can also be used to gain access to the device and provides access to the Linux operating system.
Recovery mode
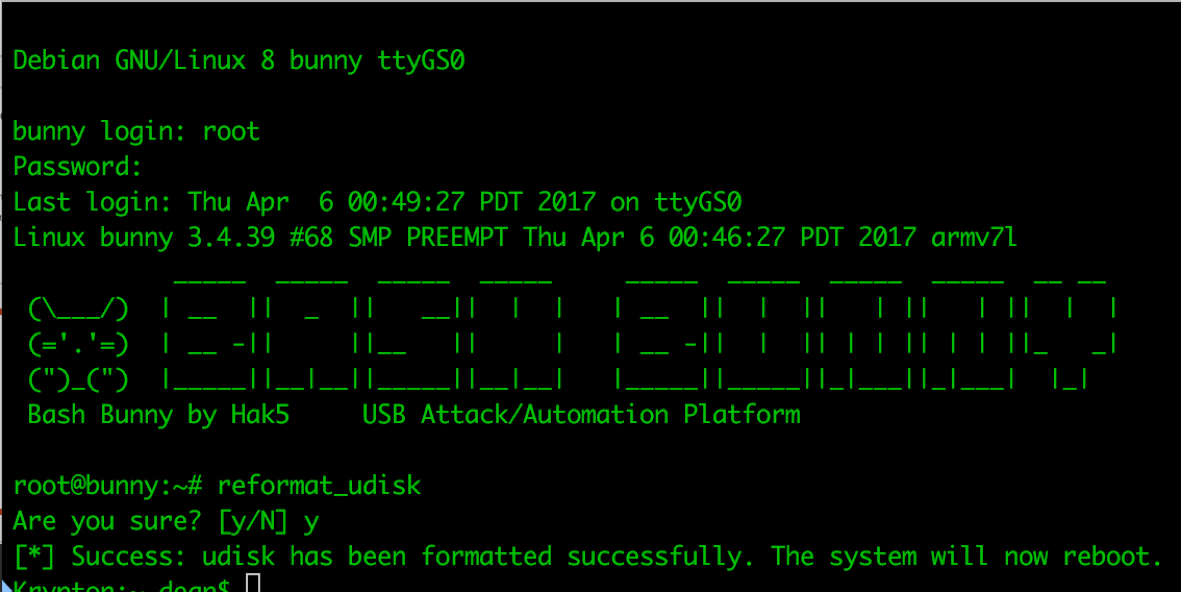
Given that the device generally is presented as mass storage during arming and as required by payloads, it is possible that you can ruin your configuration by deleting files amongst others.
Luckily there is a recovery mode and the option to reformat the mass storage.
Additional information
Should you wish to discover more about the Bash Bunny yourself, we can thoroughly recommend the the following community resources: