Sophos provide Anti-Virus solutions for a number of platforms, including Windows, Mac and various flavors of Linux and Unix. This blog post however details a potential privacy concern when the “Web Protection” component is enabled within the Sophos Endpoint Security and Control software, which features within Sophos Anti-Virus for Windows (version 10.3.x).
This is not something new, however I personally only discovered this recently whilst looking at the product and thought that others may benefit from the information.
At this point I would also like to state that Sophos have informed Portcullis that they are aware of this issue and will be addressing it in a future version.
What is “Web Protection”?
“Web Protection” is described as follows within Sophos Anti-Virus Help:
“Sophos Web Protection provides enhanced protection against web threats by preventing access to locations that are known to host malware. It blocks endpoints access to such sites by performing a real-time lookup against Sophos’s online database of malicious web sites.” (Sophos Endpoint Security and Control Help / About Sophos Endpoint Security and Control).
Why can enabling “Web Protection” cause a potential privacy concern?
When it is enabled and a user visits a web site, the URL is sent to Sophos’ online database where a check is performed to determine if the site is known to be malicious. If the web site is not deemed to be a known malicious web site then the user will not be prevented from accessing it, however if the web site is found to be malicious Sophos will block access and provide the user with a page similar to that shown below:
As a result of this, if your organization is more concerned about privacy than a check being performed to determine if a web site being visiting is known to be malicious or not, then `Web Protection’ should be disabled. This is due to the fact that whilst “Web Protection” is enabled, Sophos will have knowledge of the web sites that you are visiting.
How is this information sent to Sophos?
When a user visits a web site a subsequent GET request is automatically sent to Sophos’ online database containing the URL that the user is attempting to visit. However, the URL is encoded using ROT13, a simple letter substitution that replaces letters with those that are 13 positions ahead in the alphabet.
Lets take a look at an example.
When a user browses to https://labs.portcullis.co.uk, the following request is then automatically sent to Sophos’ online database to confirm that the web site is safe to access:
- http://http.00.s.sophosxl.net/V3/01/ynof.cbegphyyvf.pb.hx.w/
The initial part of the above URL “http://http.00.s.sophosxl.net/V3/01/” and the end of the URL “.w” remain static when these requests are submitted to Sophos. It is only the part of the URL between these static points which contains the ROT13 encoded version of the URL that the user is attempting to access. Let’s decode the ROT13 encoded part of this URL, using the following command:
$ echo ynof.cbegphyyvf.pb.hx | gcipher -C Rot -k 13 labs.portcullis.co.uk
The response from Sophos, as shown below, indicates that the site is not malicious and therefore allows the user to continue to the web site:
HTTP/1.1 200 OK Content-Length: 20 w l h 06 109100713
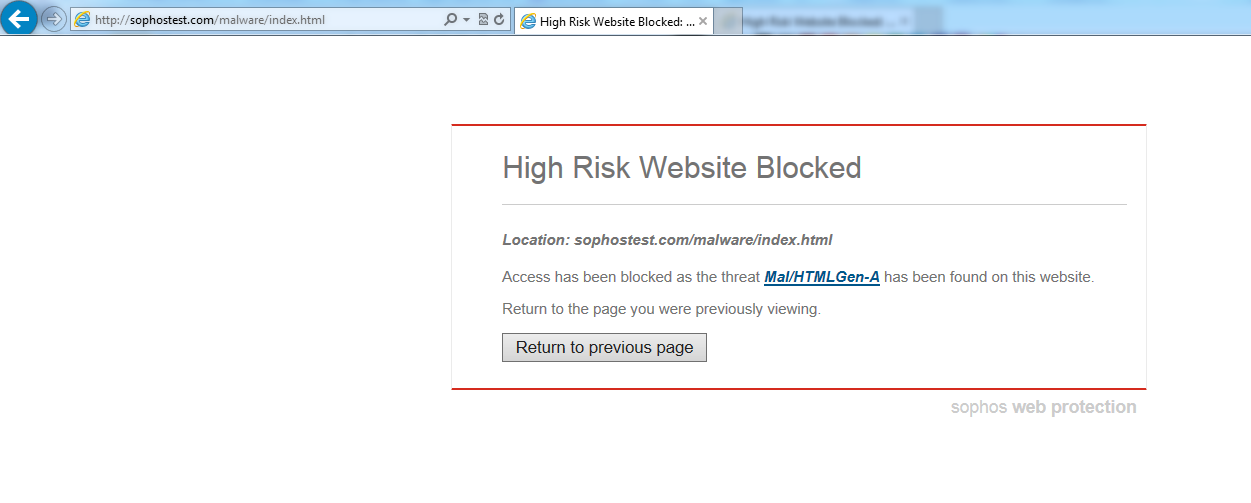
If however the user browses to a malicious web site, for example the Sophos test web site located at http://sophostest.com/malware/index.html, the response will look similar to the following and will result in the user being blocked from accessing the web site (and will be shown a page similar to that depicted in the screenshot shown earlier within this post):
HTTP/1.1 200 OK Content-Length: 28 w h p 13 101 Mal/HTMLGen-A
It is noted that all requests submitted automatically to Sophos when “Web Protection” is enabled are sent over the plain text protocol HTTP. This includes SSL links that the user is attempting to visit. For example a user visiting https://www.hotmail.com would result in the following request being submitted to Sophos http://http.00.s.sophosxl.net/V3/01/jjj.ubgznvy.pbz.w/. If you wish you can decode this URL yourself using the method described earlier in this post!
Finally, it is noted that requests submitted to Sophos do not appear to include query parameters, however I have observed directory names included within requests.
How to disable “Web Protection”
Before detailing the steps that can be taken to disable “Web Protection” it is worth pointing out that Sophos do not advise disabling this feature, as they believe this will reduce the level of protection provided by their product. It is therefore advised that a risk assessment be conducted to ensure that the benefits of disabling this feature outweigh the risk of keeping it enabled for your particular environment.
The following steps can be taken to disable “Web Protection”:
- Open Sophos Endpoint Security And Control
- Click “Configure” in the menu bar and select “Anti-Virus > Web Protection”
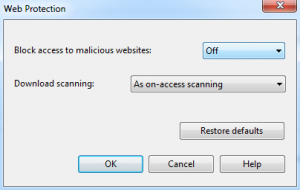
- A new window will appear, as pictured below
- Ensure “Block access to malicious web sites” is set to Off
- Click “OK”